
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
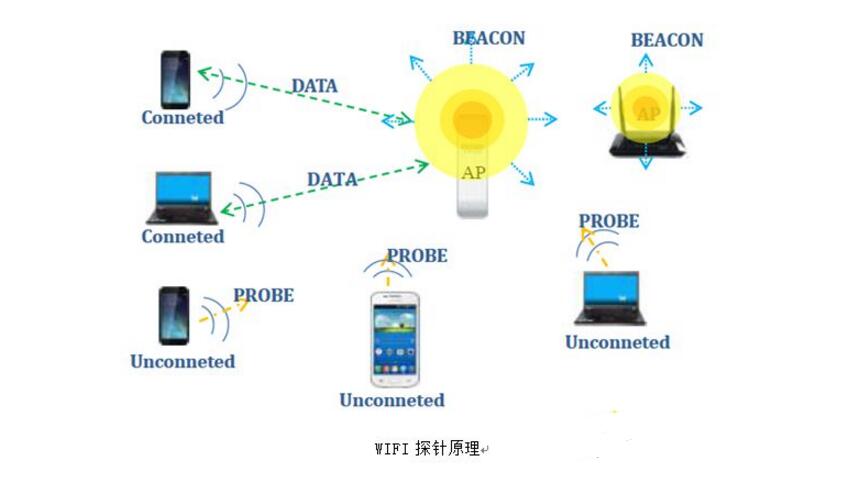
When one device sends information to another device through wireless transmission technology, other similar devices around it can receive wireless information. The WiFi probe technology is based on this principle. Specifically, when the WiFi device is within the listening range of the WiFi probe, when the WiFi device (whether a terminal, a router, or other WiFi device) transmits any frame, the probe can be intercepted regardless of the sender. And analyze some information of the MAC layer and the physical layer of the frame, such as the MAC address, frame type, and signal strength of the transmitting and receiving devices. The WiFi probe does not need to have any interaction with the surrounding devices, and does not emit any WiFi signal itself, that is, realizes the sensorless acquisition of MAC information.
The network protocol used by the WIFI probe is the IEEE 802.11 protocol suite, which contains many sub-protocols. Among them, they are developed in chronological order, mainly:
(1) 802.11a
(2) 802.11b
(3) 802.11g
(4) 802.11n
In network communication, data is encapsulated into frames (a block of data in communication). Frames are fixed in the data link layer transmission, and can be transmitted without random packaging and packaging. The size is limited, the minimum is 46 bytes, and the maximum is 1500 bytes.

1. Statistics and analysis of real-time passenger flow, mastering offline population data, and providing valuable passenger flow data for merchants.
2. Use the detection data to interface with the user information to achieve offline marketing, such as crowd portraits.
3. Public safety business, engineering, etc., as a supplement to urban security.
4, employee attendance, employee tracking, etc., enterprise attendance data accurate attendance, WiFi probe can help implement, such as automatic punch.
5, VIP customer reminder, such as help offline shopping guide sales.
6, family care, family reminders, etc.

1. Massive collection: Wi-Fi probes cover a wide range of coverage, and can collect MAC addresses in the range. At the same time, data is not restricted, and Mac addresses can be collected in large quantities.
2. Real-time data transmission: Wi-Fi probe can realize real-time data transmission, and monitoring data can be transmitted back in real time;
3. Identity matching: The MAC address is used as the unique identification code of the mobile phone, and can be matched with other data to achieve identity matching;
use:Security warnings, regional hotspot maps, crowd trajectories, criminal detection, and flow monitoring.

Business architecture
June 28, 2024
Wyślij je do tym dostawcy
June 28, 2024

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.